Security Fundamental Concepts
In the world of network security (as in every other environment) it is important to ensure that the meaning of concepts is agreed and understood by all participants. If the same concept means different things to different parties… there will be misunderstandings! So let’s go through a few key security concepts widely use in Cisco environments and explain what their official meaning are.
CIA triad
This concept is the foundational basis for many security doctrines:
• Confidentiality: only users who need access to certain data should get that access
• Integrity: data cannot be tampered with by unauthorised users
• Availability: networks/systems/data should be accessible to all authorised users all the time (or as close to it as possible)
Attackers can threaten one or more of these 3 principles and security is there to prevent that.
Vulnerability, Exploit, Threat & Mitigation
• Vulnerability: any potential weakness that can threaten the CIA of systems/data
• Exploit: tool (software, hardware, etc) that can be used to exploit a vulnerability
• Threat: potential of a vulnerability to be exploited
• Mitigation: technique/device/etc that protects systems/data against threats
Vulnerabilities (e.g. buffer overflow in a software we use) need exploits (e.g. binary crafted to use a given vulnerability to escalate privileges) and a threat (e.g. malicious hacker using the vulnerability exploit) to materialise.
Mitigation techniques are meant to tackle threats in a myriad of ways: firewalls, patches, encryption, VPNs, 2FA, etc.
Common attacks
• DoS or Denial of Service: those that threaten the availability of the system by overwhelming it in some way (e.g. TCP SYN flood attack). Nowadays, DoS are rarely successful as the source of the attack should be easy to identify and block. Far more common are DDoS (Distributed DoS) in which the target is overwhelmed by a large number of attackers (most often unwilling/unknowing 3rd party devices infected by malware -> bots)
• Spoofing: those that fake the source of the attack to sow confusion or impersonate other systems
• Reflection: those in which the attacker sends traffic to a reflector and spoofs the source address so that the reflector replies to that spoofed address
• Amplification: these are reflection attacks in which the amount of traffic sent to the reflector is dwarfed by that forwarded to the spoofed target. The larger the amplification factor, the easier/faster it will be to take down the target.
• Man-in-the-Middle: those in which the attacker places himself between the source and destination to snoop on communications or to modify the data before it reaches the destination.
• Reconnaissance: these might or might not be attacks per se and they are meant to gather information on the target (e.g. nslookup, whois, nmap, etc)
• Malware: malicious software (e.g. viruses, worms, trojan horses, etc) that usually infect a user’s device without his knowledge or consent.
• Social engineering: attacks that prey on people’s ignorance, credulity or goodwill to extract valuable information (e.g. passwords, IDs, etc)
• Password related: brute force, rainbow tables, educated guesses, etc
Multifactor authentication or MFA
The old fashion username & password authentication is awfully inadequate with high value targets for obvious reasons: weakness! It has long been replaced by multifactor authentication (2FA or 3FA) in which a username or ID must be used together with:
• Something you know: password, passphrase, PIN, answer to question, etc
• Something you have: card PIN reader, RSA token, Yubikey, etc
• Something you are: mostly biometrics such as fingerprint, face scan, palm reader, retina scan, etc
MFA makes it much harder to access the protected system as the attacker would need to get his hands on that something you have… or physically coerce you!
Digital Certificates
Digital Certificates are another form of authentication used to prove the identity of the holder of the certificate. They are most commonly used to prove the legitimacy of websites but can also be used in server/client interactions to prove both sides are legit.
Entities that want certificates to be trusted by the public need to prove their identities to a CA (Certificate Authority) and send them the CSR (Certificate Signing Request), in order to get the certificate.
Triple A
Triple A or AAA stands for Authentication (verify a user’s identity), Authorisation (verify & enforce the privileges the user has) and Accounting (recording users’ activities for accounting, auditing, security and other purposes).
In the network environment AAA servers usually use one of the following two AAA protocols:
• RADIUS: open standard protocol that uses UDP ports 1812 + 1813.
• TACACS+: Cisco proprietary protocol that uses TCP port 49.
Security Program Elements
Any serious security program will need to include at least the following items:
• User awareness: programs designed to make employees aware of potential security threats and how to tackle them (e.g. false fishing emails to catch unaware users)
• User training: formal programs intended to educate employees on the company’s security policies, potential threats, dos and don’ts, etc
• Physical access control: keylocks, badges, fingerprints, etc
Remote Access and VPNs
WAN or Wide Area Network is generally a network that interconnects various LANs over a large geographic area. WANs are typically used to interconnect the various datacenters, offices and other sites belonging to the same company, so they are private networks.
Most WANs used either of these two:
• Leased Lines (dedicated physical links, usually optic fiber) that use PPP or HDLC encapsulation protocols. Examples: T1 (1.5Mbps), T2 (6Mbps), T3 (44Mbps), E1 (2Mbps), E2 (8Mbps), E3 (34Mbps), etc.
• MPLS VPNs or Multi Protocol Label Switching that use Ethernet. These are far more common due to their far lower cost that stems from their shared nature.
In MPLS there are 3 types of routers: CE (Customer Edge Router), PE (Provider Edge Router) and P (Provider Core Router). When PE routers receive packets from CEs, they add a label to the Ethernet frames to identify their provenance and determine their destination within the Service Provider network. When those frames reach the PE router on the other side, the labels are removed and the frames forwarded to the customer’s CE router. Therefore, CE routers do not run and are totally unaware of MPLS.
MPLS VPNs can be created at Layer 2 or 3 of the Ethernet protocol. When using layer 3, the PE routers on either side of the Service Provider do OSPF peering to learn each other’s topology. We can also use static routes but that is less common.
When using layer 2, the routers and network of the Service Provider are totally transparent to the customer. Both CE routers will OSPF peer as if they were directly connected.
Private WAN services such as leased lines and MPLS provide security because each customer’s traffic is separated by using dedicated physical connections (the former) or labels (the latter). Additionally, there should be some kind of SLA (Service Level Agreement) that guarantees certain bandwidth, latency, etc. The downside of private WANs is cost. Depending on the distance to be covered or the bandwidth requirements needed, the cost might be prohibitive. That’s where Internet VPNs come into the picture.
There are two kinds of Internet VPNs:
• Site-to-site using IPsec: a VPN tunnel is created between 2 routers by encrypting & encapsulating packets with a VPN header and a new IP header. The 2 headers and removed on the receiving router, the packet decrypted and forwarded to its destination. This IPsec tunneling is transparent to all other devices who are unaware of it. One shortcoming of IPsec tunnels is its inability to handle broadcast and multicast traffic. It can only handle unicast packets. So protocols like OSPF that rely on multicasting cannot be used over IPsec. A way to overcome this limitation is to use GRE-over-IPsec. GRE stands for Generic Routing Encapsulation, it can handle uni/broad/multicast packets and a myriad of protocols but it does not encrypt traffic. By using GRE and IPsec on top, we get the best of both protocols.
• Remote access using TLS: this kind of VPN is most often used to give employees access to company systems.
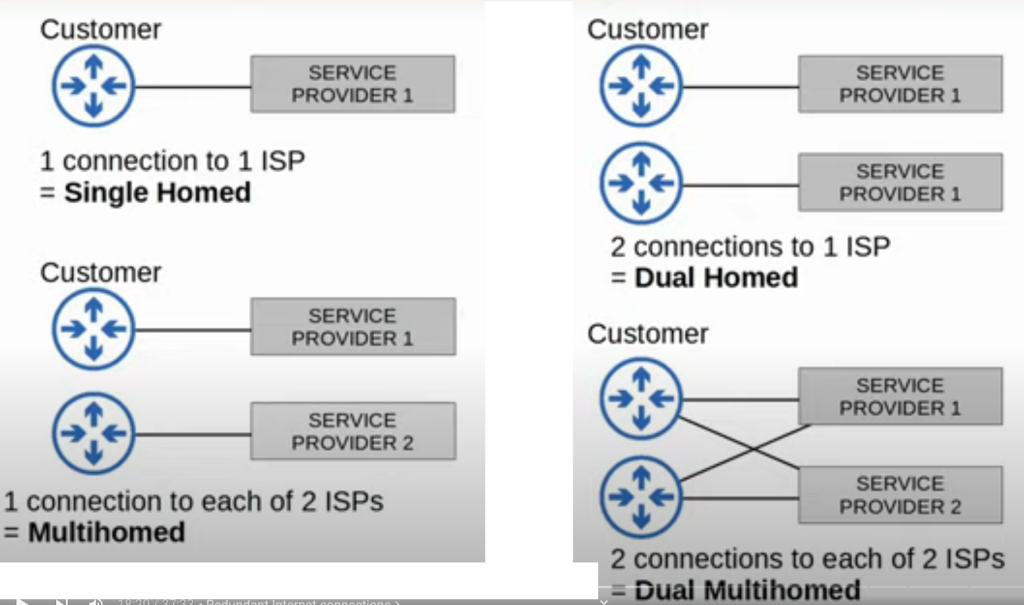
Redundant Internet Connections
There are 4 classes of redundant internet connections:
Wireless Security
In wireless networks all clients must be authenticated before they can be associated with an AP (Access Point). Additionally, clients should also authenticate the AP to avoid associating with rogue APs. This authentication can be done with:
• Passwords
• Username & password
• Certificates
Furthermore, all wireless traffic should be encrypted to prevent any listener within range from reading it. Encryption keys should be used on a per-client basis so that traffic meant for a given client cannot be read by the rest. There can also be group keys for traffic meant for groups of clients.
Finally, all packets should use MICs (Message Integrity Checks) to ensure they are not tampered with.
There are 7 authentication methods that can be used in wireless networks:
• Open Authentication
• Wired Equivalent Privacy or WEP
• Extensible Authentication Protocol or EAP
• Lightweight EAP or LEAP
• EAP Flexible Authentication via Secure Tunneling or EAP-FAST
• Protected EAP or PEAP
• EAP Transport Layer Security or EAP-TLS
Open Authentication is no authentication at all: clients send connection requests and they are accepted without further ado. But once the client has associated with the AP, another authentication method can be enforced before network access is granted (e.g. WiFi from hotels, conferences, cafes, etc).
WEP provides authentication and encryption using the RC4 algorithm but it is old can very insecure for today’s standards.
EAP is an authentication framework that defines a standard set of functions used by the 4 subsequent EAP methods. EAP incorporates the 802.1x standard that limits network access to clients until they authenticate. In 802.1x there are always three entities: Supplicant (the client), Authenticator (the AP) and Authentication Server (the device that checks credentials and permits/denies access).
LEAP was developed by Cisco as an improvement over WEP and it uses username+password to ensure mutual authentication: both client and server challenge each other by sending a phrase and checking the encrypted response. Additionally, the WEP keys used are changed frequently to make decryption harder for attackers. LEAP is also insecure and should not be used.
EAP-FAST was also developed by Cisco and it establishes a secure tunnel via a PAC (Protected Access Credential) sent from the server to the client. The authentication takes place inside this tunnel.
PEAP also establishes a secure tunnel à la EAP-FAST but it uses a digital certificate instead of a PAC.
EAP-TLS also establishes a secure tunnel but requires certificates for both client & server. It is thus more burdensome and can only be used with vetted clients who then get their certificate.
Wireless Encryption and Integrity Methods
TKIP or Temporal Key Integrity Protocol was developed due to the shortcomings of WEP. It adds:
• a MIC to protect the integrity of the messages and includes the MAC of the sender
• a key mixing algorithm used to create a unique WEP key for every frame
• an initialisation vector that is doubled in size from 24 to 48 bits
• a timestamp to prevent replay attacks
• a TKIP sequence number
TKIP is used in WPA version 1.
CCMP or Counter/CBC-MAC Protocol was developed after TKIP, is used in WPA version 2 and is obviously more secure. It uses two different algorithms (AES and CBC-MAC) to provide encryption and MIC.
GCMP or Galois/Counter Mode Protocol is more secure and efficient than CCMP and is used in WPA version 3. It also uses AES for encryption but for MIC it uses GMAC (Galois Message Authentication Code). Among other improvements, WPA3 adds PMF (Protected Management Frames), SAE (Simultaneous Authentication of Equals) and Forward secrecy to prevent frames being captured and decrypted afterwards.
